Thank you for selecting BajEye as the solution to your online
activity management needs. BajEye is
easy to install. Simply insert your BajEye 4.0 installation CD. If you downloaded BajEye from the web,
simply launch the bajeye40.exe installer program. This will walk you through the software
installation, with step-by-step instructions.
IMPORTANT: If you have a
previous version of BajEye installed, please refer to the section on Upgrade
Installations.
Once you have installed BajEye, you will find a new program group, BAJAI, in your start menu. The BajEye Activity Manager Configuration Console
program (simply referred to as Console in the rest of this document) is located
there. You can navigate to it by selecting
Start -> Programs
-> BAJAI-> BajEye
You may have also
installed a shortcut on the system desktop. Selecting the program BajEye Console will
launch the console program and place the BajEye icon in the system tray. (The system tray is on one end of your
taskbar, usually at the bottom right of the screen. You will notice the clock is also in the system tray.).
NOTE: Filtering is NOT enabled by default. You MUST run the BajEye Activity Manager
Configuration Console and customize your settings after you have installed the
program. When you run the program for
the first time, you will be asked to select an administrative password. Once the password has been set you can
access the console from the system tray icon.
NOTE:
In order to unInstall the BajEye software, you MUST
run the BajEye Console at least once to set up an
administrative password.
Following the
prompts of the installation program completes your first time installation of BajEye. Upon the completion of the installation, you
are ready to configure your filtering criteria using the BajEye
Console.
You should
carefully read and understand this section if you are performing an upgrade
installation. If you have performed
the installation for the first time, you can skip to the section “Using The BajEye Configuration
Console”.
If you are already
a current user of BajEye, you perform upgrade
installations by simply installing over the previous version of BajEye. You should NOT uninstall the
previous version, as you will loose you current access management
settings.
IMPORTANT: It is important that you make sure you have disabled the BajEye
Activity Manager BEFORE INSTALLING AN
UPGRADE.
During an upgrade,
the installation will try to disable the filtering mechanisms so that an
upgrade can occur. It is strongly
recommended that you close all network and Internet applications before
continuing the upgrade installation.
The installation will notify you if there is a need to reboot the system
BEFORE installation can complete, however the instructions below outline the
necessary steps.
Because BajEye
hooks itself into your systems TCP/IP stack, it is important to
ensure that you have deactivated the access management mechanisms. You can do this by opening the BajEye
Console and ensuring that the “BajEye”
checkbox is NOT checked.
See the screenshot below.
IMPORTANT
TO CHECK PRIOR TO AN UPGRADE
|
|
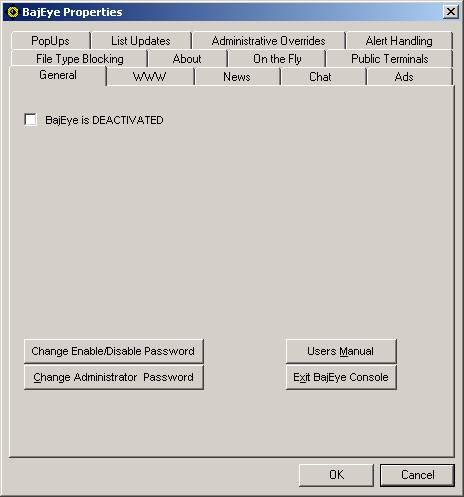
<1-1> Prior to BajEye
Upgrade – Ensuring the BajEye Activity Manager is NOT
ACTIVE.
If you are
deactivating the BajEye Access Manager manually, you
should also reboot your computer BEFORE you
attempt the upgrade installation. The
reason for this is because the BajEye Access Manager mechanism is
activated during boot up. It hooks itself into the TCP/IP stack during this
boot up procedure. Any Internet
protocol, such as DHCP for example, that is used during boot up will cause the
mechanism to be installed into memory.
In this situation, the installation will fail to copy the files properly
because the old files are in use by the system.
IMPORTANT: Before installing an upgrade, you must make
sure that the BajEye Activity Manager is NOT
ACTIVE. A reboot before installation
may be necessary when you deactivated the Activity Manager. The installation will try to detect any
problems and notify you. See figure 1-1.
NOTE: In order to unInstall the
program, you must have run the BajEye Management Console once to
set up an administrative password.
IMPORTANT: BajEye was designed to be removed
only by the administrator and ONLY using the unInstall tool. BajEye is quickly and cleanly
uninstalled by using the unInstall applet found in program group BajEye in your start menu. You can navigate
to it by selecting:
Start
à Programs à
BAJAIà BajEyeà unInstall
When
using the uninstall process you will be asked for the BajEye
Console administrative password.
Correct entry of the password will allow the uninstall to continue.
Should
the BajEye software installation be tampered with, it is
possible that the TCP/IP stack will become corrupt. Depending on the knowledge level of the person attempting to
tamper with the controls, your options are:
1. You
can try to reinstall the BajEye software and reboot your
system. This may return your system to
its proper settings. Note that this
will only work when minor tampering attempts have been made to BajEye. This is best done in Windows “Safe Mode”
without network capability.
2. You
can call BajEye technical support and we will do our best to
help you with resetting your TCP/IP stack.
Severe tampering of the software may require that you refer to option 3.
3. Should
a more sophisticated attempt to tamper with the BajEye software
take place, it is most likely that the TCP/IP stack will be corrupted.You will
require Windows administrator privileges to correct this. It is important to understand that a
complete reinstallation of Windows is NOT necessary, you only need to
reinstall the networking components.
In the case where the networking aspect of
your computer system is not working and BajEye is installed, determining
whether tampering has occurred should be investigated before Microsoft, BAJAI,
or the provider of a communications device are contacted.
IMPORTANT: BAJAI
technical support will not be provided for demonstration versions of BajEye
software that have been tampered with. If you are considering BajEye for your activity management
needs and are planning to evaluate the security mechanism (i.e. attempt to
bypass BajEye) it is recommended that you first contact
BAJAI to be placed on our support exception list. We would be pleased to hear about any attempts to circumvent the BajEye
software and the details of the end results, either successful or
not. Clearly the security mechanisms in
place on any computer help to ensure the security of the system as a whole.
You can start the Bajai Console from the start Menu:
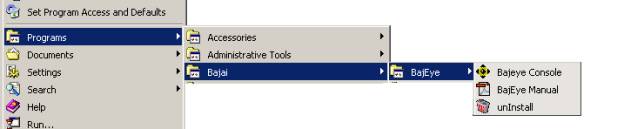
When you select the BajEye console, the program is started
and a BajEye icon will appear in your system tray.
You can configure BajEye by clicking on the BajEye icon in the system tray. After Clicking on the BajEye
icon, you will be prompted for the administrative password. The first time you run the BajEye console,
you will be asked to enter an administrator password.
|
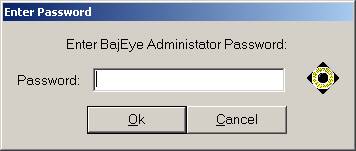
<3-1> Enter Password prompt
|
Once you have successfully logged in to the console, you are
ready to begin configuring BajEye to
suit your online activity management needs.
The BajEye Console
program can only be accessed via the icon in the system tray. By default when you invoke the program from
the start menu, it runs minimized in the system tray.
The OK and Cancel buttons refer to the entire
settings. Clicking OK will place your changes to the activity management criteria in
place, while clicking Cancel will
discard your changes. See figure 3-2.
The various tabs in the BajEye
Console
allow you to navigate to all the software features and options. The General tab allows you to
ACTIVATE or DEACTIVATE the BajEye Activity
Manager.
By clicking the “BajEye”
checkbox, you can toggle the system level management on or off. The message to the right will help you
determine if the BajEye Activity
Manager is ACTIVED or DEACTIVATED

<3-2> BajEye Options – General Tab
The “Exit” button is the only way to remove the BajEye Console
Program from memory. This will also
remove the
BajEye icon from the system tray.
The “User’s Manual” button will bring up this manual.
The “Change
Enable/Disable Password” button will allow you to change the password that
allows 2nd level administrators to ACTIVATE or DEACTIVATE filtering.
The “Change
Administrator Password” button will allow you to change the administrator’s
password.
BajEye gives you a high degree of control over the types of
media that can be accessed via the World Wide Web (http). In the “Web Access Options” box, the check
box labeled ‘Manage Web Access' is a switch that allows you to turn web content
filtering on and off. Below the check
box is a list of the BAJAI List content categories. Content categories are alternately selected and de-selected by
double clicking the category. There are
two indicators of the access status of each category.
|
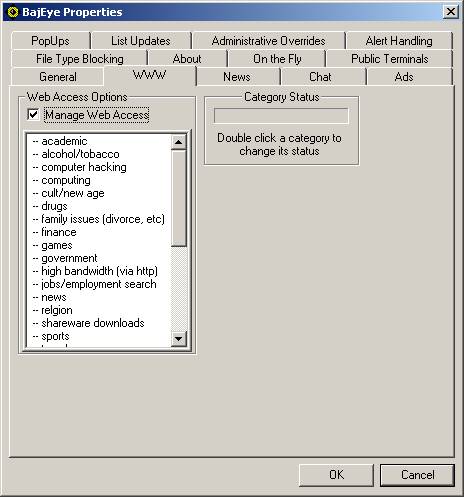
<3-6> Configuring WWW settings
|
One indicator of
a category’s status is in the status box to the right of the content
list. It will display the category’s
status information. For example, the category ‘weapons’ may have status -
CANNOT BE ACCESSED.
The second
indicator is the glance indicator that allows you to quickly see the status
of a category. Each category with a
‘++’ in front of it indicates that access IS being restricted and a ‘--‘ indicates that it is NOT being
restricted. Categories set to ‘++’ are moved to the bottom of the scroll down
list.
|
You can manage access to newsgroups that contain adult
content by selecting the check box.
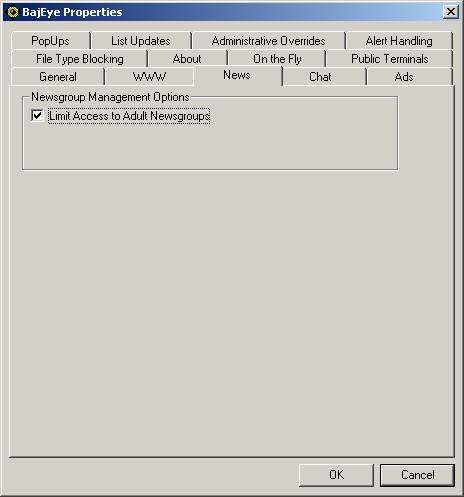
<3-7> Newsgroup
settings
BajEye allows you two
methods to manage chat protocols. You
can prevent the use of certain protocols, or you can filter the text-based
information of IRC. You specify which text strings to filter out of chat
sessions on the Administrative Overrides tab.
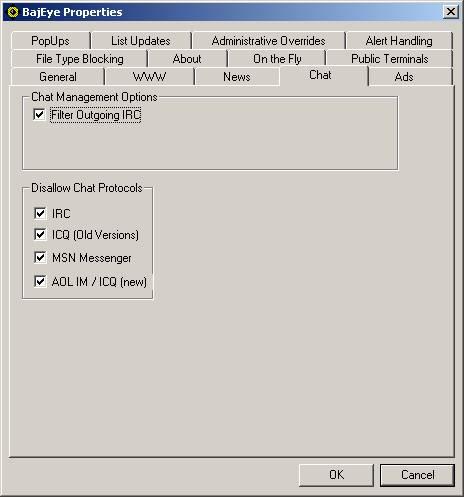
<3-8> Chat settings
BajEye allows you to prevent the use of four of most popular
chat protocols. IRC (Internet Relay
Chat), ICQ, MSN Messenger, and AOLs Instant Messenger.
The filtering of
information going out of your computer on IRC (other protocols are coming soon)
is also possible. Administrators can
configure this to prevent keywords that describe the company’s intellectual
property from being given out through a chat channel. It is also configurable to prevent ANY information from being
disseminated over a chat protocol. The
chat information filtered is configured in the ADMINISTRATIVE OVERRIDES tab.
Ads/Spyware/Malware
Advertising banners are not just flashing nuisances, they
also consume bandwidth. By blocking
advertising banners, you free up more of your valuable network bandwidth.
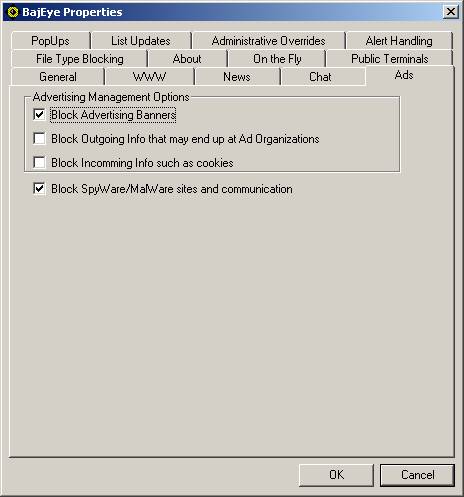
<3-9>
Advertising settings
Blocking out going information that may be used by
advertising organizations allows you to mask the information in the following
fields:
1.
Referrer - This field usually contains information about where
you were before going to the next site.
2.
User Agent - This field usually contains information about
what browser you are using
3.
Cookie - This field usually contains information that was
stored in a cookie that the site will use during your visit.
Blocking
communication from spy-ware and mal-ware sites will prevent contact to servers
that track surfing habits and utilize malicious code.
NOTE: Some interactive sites that
use Java and JavaScript may not work properly because this information is
scrambled by the BajEye filter. HOTMAIL
for instance REQUIRE the Cookie and User Agent information in order to work
properly.
Blocking incoming information allows the BajEye filter to scramble the cookie
information BEFORE it gets stored on you machine. This option will cause some interactive sites to be less user
friendly since the cookie information they usually gather is scrambled.
Pop-up filtering gives control of your PC back to you. By blocking the Java open.window event, you
can be sure that sites cannot open windows or perform other tasks when you
visit a web site. Sites that use
advertisers or generate click-through revenues commonly do this. Typically this manifests itself in the form
of a new window being created with an advertisement in it. See figure 3-10
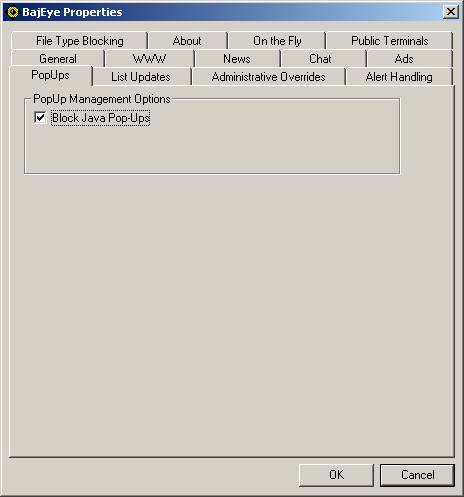
<3-10> Java
Script settings
This tab is your ultimate control over the BAJAI List of
content categories. Here you can
override blocked content categories, enter personal information that you do not
want to be broadcast in chat channels, and more.
You can add and remove sites to the “Blacklist” and the
“Whitelist”, and chat information in the “Block Outgoing” list. Whitelist items are signified with a white
button, and blacklist items are denoted with a black button. Chat information that is to be filtered on
outgoing packets is denoted with a standard 'no entry' sign. In figure 3-11,
the BAJAI website is on the white list, while ‘nakednews’ is on the blacklist,
and the name ‘Maggie Simpson’ will not be broadcast onto an IRC chat channel.
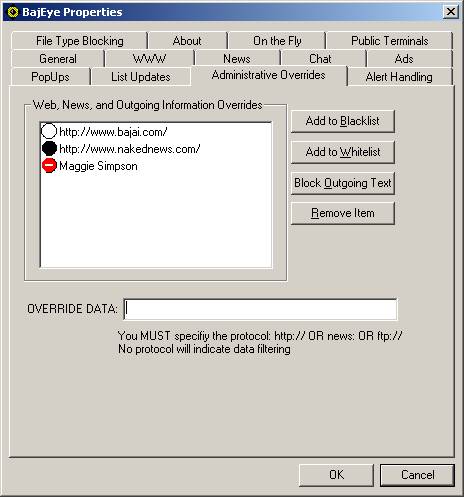
<3-11>
Configuring override information.
Enter the information (URL or data to block) into the
‘OVERRIDE DATA:’ field and click on the appropriate button; “Blacklist”,
“Whitelist” or “Blocked Outgoing”. It
is important that when you are administrating the URL overrides, that you
include the protocols. Web sites should
be prefaced with “http://”, while
newsgroups would be prefaced with “news:”.
Any item not prefaced with a known
protocol will be assumed to be a URL and will automatically be prefaced with http:// . “Blocked Outgoing” information does not need a protocol preface.
You MUST register your new copy of BajEye software with BAJAI. After doing so, you will receive a
16-character registration code from BAJAI.
Enter this code in the field provided under the ‘Register’ tab and click
the “Register” button. Changes will
take effect once you click the “OK” button.
You will have to exit and restart the BajEye Console. Once
you have registered your copy of BajEye, the ‘Register’ tab is replaced by the ‘List Update’
tab.
If you have installed this BajEye software as an upgrade to a previous version, you will not see the
‘Register’ tab.
BajEye software
relies on the BAJAI List of content categories, a complete indexation and
categorization of the Internet. BAJAI’s
IajaBot software robots continuously scour and categorize the Internet, adding
new web sites to BAJAI’s list and deleting obsolete sites. BajEye remains
effective, in an ever-changing Internet environment, by regularly synchronizing
with the BAJAI List. This also allows BAJAI to notify you when new releases of BajEye software are made available.
BajEye
can contact BAJAI’s List Update Server and make any changes to the BajEye software. A progress meter indicates the status of the local update.
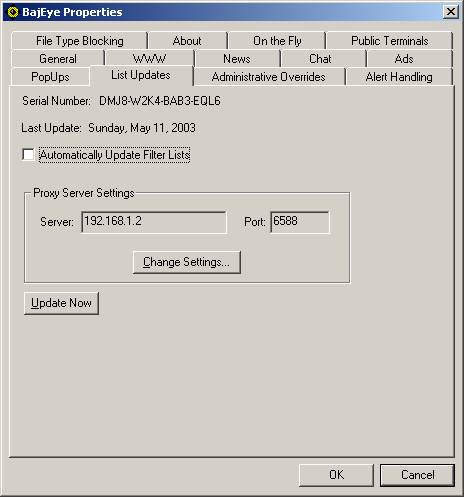
<3-12> List
Updates settings
To configure BajEye to
perform automatic, daily list updates, select the “Automatically Update Filter
Lists” option. List updates will be
performed in the background, once daily. The text beside the ‘Last Updated:’
field reflects the date when the last update occurred. If the BajEye
software cannot reach the BAJAI List Update Server via the Internet at the
scheduled time, it will attempt to do so the next time an Internet connection
is established.
List updates occur in the background and failures due to
lost or missing connections prevent the update from happening. When laptop resources are on the road, the
list will update automatically when the computer goes online. As soon as the computer connects to the
Internet, BajEye automatically
performs a list update. This will help
to ensure that laptops are always up to date.
BajEye will
perform an immediate list update when you select the ‘Update Now’ button. The
text beside the ‘Last Updated:’ field reflects the current date. Should you have automatic update selected
and the date is not current, you should select the ‘Update Now’ button.
If you are using a proxy server to connect your computer to
the Internet, you will need to select the ‘Change Settings’ button and enter
your proxy settings. List updates will
automatically route through the specified proxy.
Automatic list updates are performed using a service called
LISTSUB. The BajEye
console will try to create and activate the service when you
select automatic updates. Conversely it
will try to deactivate and delete the service when automatic updates are turned
off. You can check to see that the service
exists with the Services icon in the Control Panel and administer it from
there.
To manually install this service, perform the following
commands from a DOS prompt:
C:><PATH_TO_BAJIACON>listsub
-create
C:
:><PATH_TO_BAJIACON>net start
“listsub – EyeUpdate”
To manually remove this service, perform the following
commands from a DOS prompt
C:
:><PATH_TO_BAJIACON>net stop “listsub – EyeUpdate”
C:><PATH_TO_BAJIACON>listsub
-delete
This service will keep the BajEye
lists up to date for registered users.
There are several
ways in which BajEye can response to user policy violation
attempts. The default handling is to
bring up the ‘Access Restricted’ message window, which presents information
regarding the restricted action.
You can suppress
all pop-up alerts by selecting the ‘Silent Mode’ option.

<3-13> Configuring violation handling
policy
As an alternative
to using the default message alert, the user’s browser can be redirected to an
alternate website. This feature allows
administrators to redirect a user violation to an Internet Use Policy Page,
which carries information regarding appropriate use of company resources. Select the “Use Alternate Notification URL”
option and enter your URL in the field provided.
You can also choose
to log any violations that occur by selecting the “Log Violations” option. For Windows 95/98 environments, the event
log is kept in the ‘Program Files\BAJAI\bajaicon’ directory. In Windows
NT/2000/XP, the logging is done through the event logger and can be viewed
using the Event Viewer tool that is available as a default administrator’s tool
and comes with WindowsNT/2000/XP.
In certain
situations, you may also want to allow users to bypass the system. By selecting
the “Allow Bypassing” checkbox, users will be offered the option to bypass the
system blocking. When a blocked site is accessed, the user will be notified and
asked if they wish to go there anyway.
Refer to figure 3-14. These
bypasses are always logged for the administrator to view them.
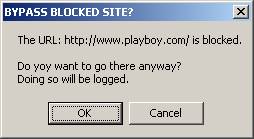
<3-14> User Prompt – Bypass Blocked
Site?
If the user clicks OK, the access to the site will
be granted, however if the user clicks cancel, access will not be allowed.
Public Terminal Alert Handling
The system
administrator can take extra measures when faced with repeated attempts to
access content that has been deemed contrary to policy. In effect, this security feature will detect
persistent attempts to access blocked content, and lock up the ability to
access the Internet until an administrative password has been entered.
For example, during a persistent attempt to
reach blocked web sites, the user would be presented with the following prompt:
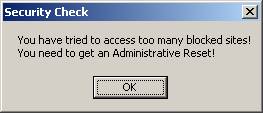
<3-15> User Prompt – Security Check
At
this point in time, all access to the Internet has been shut down, and an
administrative override is necessary.
The user of the public terminal will next be presented with the
following override prompt.
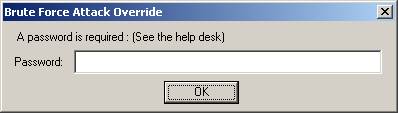
<3-16> User Prompt – Attack Override
Now, an
administrator or local help desk technician can clear the system lock up by
entering the 2nd level administrative password.
You can block
specific types of files from begin downloaded from the Internet by specifying
the file’s extension name. Type the
extension name in the ‘File Type Blocked’ field and click the ‘Add’ button.
To remove an
extension from being filtered, select the item in the ‘File Types Blocked’
field and click the ‘Remove’ button.
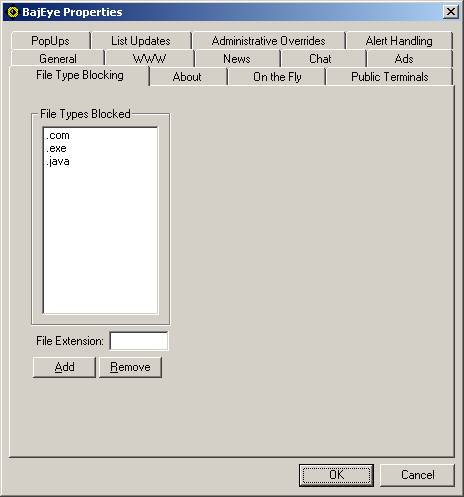
Figure <3-17> File Type Blocking tab
To get more information regarding file extension and the file
types they represent, we suggest you visit the “http://filext.com/ “.
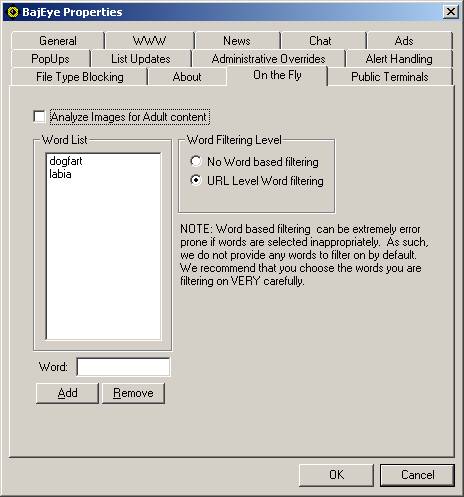 Figure <3-18> On-the-Fly tab
Figure <3-18> On-the-Fly tab
On the fly image
analysis and filtering allows you to dynamically analyze image content to
determine whether or not there is adult content. If adult content is detected, the image will not be displayed in
the web browser. The diagram below show
the results of an image search using the word ‘boobs’ on Google’s™ Image Search
engine.
On the fly word
filtering allows the administrator to specify words that, if they appear in the
URL string, will be denied access. It
is imperative that the choice of words be done very carefully as a simple
sub-string can wreak havoc. For
example, choosing the word ‘anal’ would also block sites that have the term
‘analyze’ and cause over blocking. We
do not provide and words to be filtered by default, and it is the
responsibility of the administrator to decide which words are appropriate to
use.
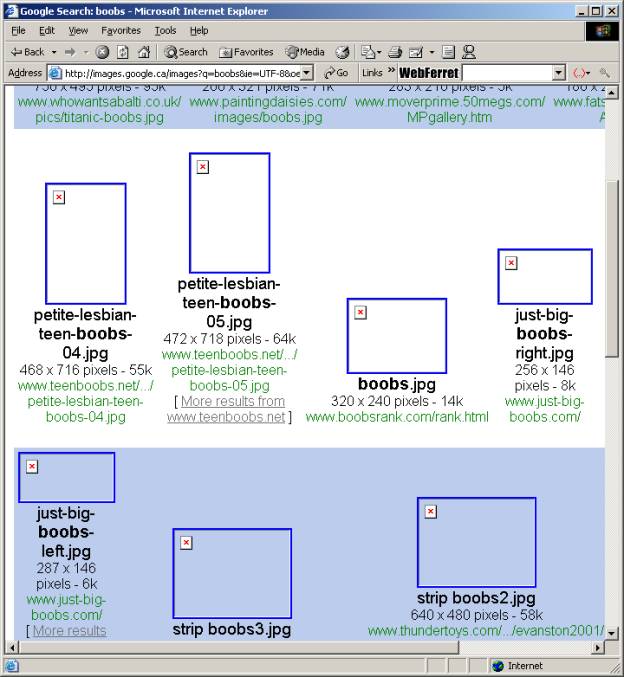
Figure <3-19> Image search on Google
with Filtered Image results
Public Terminal Settings
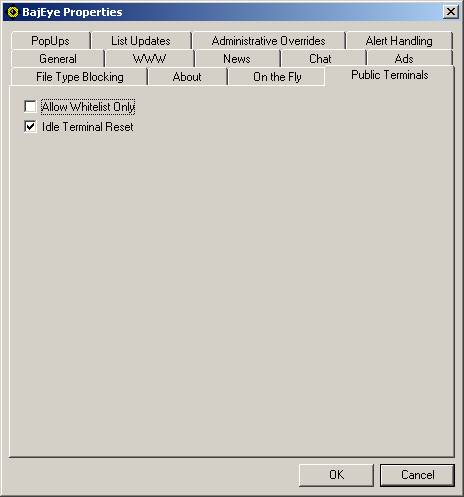
Figure <3-20> Public Terminals tab
When the “Allow
Whitelist Only” option is selected, ONLY those sites on the WhiteList can be
accessed.
When the “Idle
Terminal Reset” option is selected, BajEye will detect the activation of screen
savers, close all open browser windows, and check that BajEye
is in the ACTIVATED state.
Registered users of BajEye,
with a valid list update subscriptions, qualify for technical
support. If you run into any problems while installing or using BajEye, you can find information regarding
technical support at http://www.bajai.com/support/
or call for technical support at (613) 731-9069. A technician will promptly return your call. You may also refer to the troubleshooting
FAQ section in this manual.
If you are using a proxy server to access the Internet, BajEye will automatically recognize and filter
proxy requests. There is no need for
special configurations when dealing with proxies that are configured through
your browser.
Anonymous CGI-based surfing proxies, such as Anonymizer.com,
are proxy-like services that allow you to access the web through their web
site. These anonymous proxies send and
receive Internet requests on your behalf, which can circumvent most web
filters.
BajEye maintains
a list of anonymous surfing proxies and ALWAYS blocks access to them.
Q. I’ve installed the BajEye
software but it isn’t working.
A. After software installation, BajEye
must be configured. You
must open the BajEye Management
Console to configure the system. At
this point, you will also have to enable the BajEye
Activity Manager (see section ‘General’).
Q. When I do a search, the “searching icon”
continues to move even though the page has downloaded.
A. If you’ve activated the “Block Advertising
Banners” filtering option, this will sometimes happen. In some cases, it is helpful to just press
your browser’s ‘Stop’ button or a combination of ‘Stop’ and then ‘Refresh’.
Q. I tried the demo version of BajEye
but there were many sites that were not blocked.
A. The BajEye 15-day
demo version contains only a very small sampling of the actual Internet Index
List. The demo allows you to try the BajEye program to see how it meets your needs.
To try the blocking feature, use a common web site such as http://www.playboy.com. If you require more information about the
lists, see the BAJAI website, or contact us at sales@bajai.com.
Q. I reset my preferences in the BajEye Console but my browser isn’t
complying.
A. When you reset your preferences, you must restart
your browser to activate the new settings.
Q. I can’t get
search portals to load at all, or if they do they don’t look right.
A. If under
the “Ads” tab you’ve selected block outgoing and incoming information, the http
request to the server looking for your cookie information is incomplete and so
the responding server cannot properly complete the download. For the best
browsing experience with search portals, you can allow outgoing information and
block banner ads only.
Q. I keep getting error messages saying my list update
was incomplete.
A1. Check your hard drive for free disk space. You may have to free some disk space for
your list updates.
A2. You may have reinstalled the BajEye
program and you entered the wrong license number.
If you are having problems with your list updates, do not hesitate
to contact technical support. Often, we
monitor for problems with list updates and try to contact our customers.
Q. What is a
black list?
A. A black list is a list of web sites to which
access has been restricted. Our
Internet Index List categorizes web sites according to criteria defined by
BAJAI. Our robots actively search the
Internet for new web sites, categorize them according to their content, and add
them to our list. You can then select
categories from BAJAI’s list or you can define for your own black list of
restricted web sites (see section on ‘Overrides’).
Q. What is a
white list?
A. A white list is the list of sites that you always
want to be accessible, overriding any filtering solution. When the “Allow Whitelist Only” option is selected
under the ‘Public Terminals’ tab, ONLY those sites on the white list can be
accessed (see sections on ‘Overrides’ and ‘Public Terminals’).
Q. I own a placement agency and I don’t want my
employee’s doing job searches on my equipment, but I do want them to be able to
access our site. How do I accomplish
this if I’ve black listed job search?
A. To make an “exception” to a blocked URL or an URL
in a blocked BAJAI category, add the desired website to the white list.
Q. My browser is
trying to download banner ads, and won’t stop! What’s going on?
A. You are using Windows98. Seriously. We have
experienced the same problem, but only in Windows98! We are as mystified as you are.
Typically, hitting STOP will cause the page to appear; as well, a STOP
and REFRESH will work as well.
BAJAI currently classifies the Internet into 32
distinct content categories that you can use to manage your On-Line
Activity policies. A short synopsis of each category is given below. BAJAI
can create new categories based on customer demand.
Each URL is categorized as concisely as possible and
cross-referenced where possible. This means that certain URLs will be
classified into multiple categories. For example, the website
http://www.foxsports.com/ would be classified in the following categories:
SPORTS and TV_RADIO_MOVIES
This category contains URLs that are academic in nature.
Schools, Universities and other educational institutions are included.
This category contains URLs that contain adult oriented
themes and activities. This includes:
- Sexual
themes and erotic materials, such a writings or pictures that show or
describe sexual acts,
- Products
that are targeted at an adult market, including escorts, sex toys, strip
clubs,
- Explicit
materials be it photos, drawings, videos, audio, or textual.
·
All sites or homepages that contain a warning of adult
content or front pages that state you must be an adult to view this information
are included in this category.
This category DOES NOT CONTAIN URLs that contain educational
information about sex, sexual orientation, STDs (Sexually Transmitted
Diseases), health care issues or other medical information.
This category contains URLs that have blatant references to
drinking alcohol or smoking. URLs that contain material that glamorizes or
promotes alcohol or tobacco products.
This category contains Chat protocols (IRC, AOL, MSN), web
logs or Blogs, and discussion groups or Bulletin Boards.
This category contains URLs that have information about
computers, computing, computing science and businesses that make computer or
products for computers.
This category contains URLs that have information on cults.
This category contains URLs :
- that
have information regarding illegal drugs and drug paraphernalia
·
that contain information regarding the cover up of
usage and how to cheat drug tests
- that
contain information on substance abuse for the purpose of obtaining a
mind-altered state. e.g. glue/gas sniffing, huffing etc.
This category contains URLs that have information regarding
family issues such as divorce
This category contains URLs:
- that
have stock trading, stock tickers, banking etc.
- that
contain investment advice, money management and general financing
- with
information such as accounting, banking, insurance and mortgage
This category contains URLs that allow gambling, or contain
information about gambling such as betting tips. Lottery sites, casinos and
betting pools would fall into this category.
This category contains URLs:
- that
contain online or downloadable games, and gaming information such as tips,
cheats and codes
·
that are leisure sites such as comics, hobbies and
other leisure activities
- that
are dedicated to or are part of the computer/video game industry
This category contains URLs of municipal, provincial, state
or federal web sites. To date the list only contains Canadian and US government
URLs.
This category contains URLs that have information about
hacking computers, including information regarding the illegal use of computers
to commit crimes and URLs that contain information about how to illegally hack
passwords.
This category contains URLs:
·
that have hateful, racist or other hateful information
or otherwise promote hate
- Discriminatory
behavior based on sexual orientation, religious beliefs, race, gender,
age, abilities/disabilities or political viewpoints
- Historical
revisionists and militant groups that promote hate.
This category DOES NOT CONTAIN historical events; news or
press coverage may include the information that falls into the above
guidelines.
This category contains URLs that use high bandwidth. URLs
that contain audio/video files are included in this category. Streaming media,
and live broadcasts also fall into this category.
This category contains URLs that are job search/career
oriented. Recruiters, headhunters and other job listing sites are included in
this category.
This category contains URLs that have offer free email
services. E.g. Hotmail
This category, short for "malicious software",
contains files and executables that are software programs designed specifically
to damage or disrupt a system, such as a virus or a Trojan horse.
This category contains URLs that have current news and
recent events.
This category contains URLs that have personals ads and
dating services or advice.
This category contains URLs that have information about
religion, religious beliefs or religious related activities.
This category contains search engines such as Yahoo, Google,
AltaVista etc.
This category contains URLs that have shareware or freeware
file downloads.
This category contains URLs for shopping and online
purchasing. Auctions, retail stores and specialty shops are included in this
category.
This category contains URLs that have sports related themes.
This includes sports publications and fan pages.
This category contains the files and executables, also known
as "adware", that are hidden software program which transmit user
information via the Internet to advertisers in exchange for free downloaded
software.
This category contains URLs that are related to travel and
vacationing. This categories includes airlines, travel agents, tourist pages
and the like.
This category contains URLs relating to TV shows, radio
shows or movies. Television show fan sites, movie trailers would be found in
this category.
This category contains URLs that have information on weapons
such as guns, knives, bombs etc. URLs that promote the use of weapons or sell
weapons and related materials are included in this category.
This category contains URLs that have web cameras.
This category contains URLs that host web content for free.
E.g. Geocities, angelfire etc.
This category contains URL links to web rings. The effect is
to break the webring and prevent further surfing. E.g. webring.org.
LICENSE AGREEMENT
I. License and Use
Subject to the
following terms and conditions, we grant you a royalty-free, nontransferable
and nonexclusive right:
(A)
to use this version of BajEye
on any computer for which you are the primary user, provided that BajEye is (1) used on only one such computer
at any one time, and (2) used by one user at any one time; and
(B)
to make and distribute to others unmodified copies of the
demonstration version of BajEye,
without any direct or indirect charge (except for the cost of the media in
which the demonstration version is fixed), for non-commercial uses only.
II. Limitation of Liability
ALL USE OF BajEye IS ENTIRELY AT YOUR OWN RISK. WE WILL NOT BE RESPONSIBLE TO YOU OR ANY
THIRD PARTIES FOR ANY DIRECT, INDIRECT, CONSEQUENTIAL, SPECIAL OR PUNITIVE
DAMAGES OR LOSSES YOU MAY INCUR IN CONNECTION WITH BAJEYE
OR YOUR USE THEREOF, REGARDLESS OF THE TYPE OF CLAIM OR THE NATURE OF
THE CAUSE OF ACTION.
III. Indemnity
You will defend
and indemnify us against (and hold us harmless from) any claims, proceedings,
damages, injuries, liabilities, losses, costs and expenses (including
attorneys’ fees), relating to any acts by you in connection with BajEye, leading wholly or partly to claims
against us by third parties, regardless of the type of claim or the nature of
the cause of action.
IV. Disclaimer of Warranty
BAJEYE IS PROVIDED “AS IS”, WITH ALL
FAULTS. WE MAKE NO WARRANTIES, EXPRESS
OR IMPLIED, AS TO MERCHANTABILITY, FITNESS FOR A PARTICULAR USE OR PURPOSE,
TITLE, NON-INFRINGEMENT, OR ANY OTHER CONDITION OF BajEye.
V. Proprietary Rights
Except as
specifically licensed above, you may not copy, modify, adapt, merge, include in
other software, reproduce, translate, distribute, reverse engineer, decompile
or disassemble any portion of BajEye.
VI. Miscellaneous
This Agreement
contains the entire understanding between you and us relating to your use of BajEye and supersedes any prior statements or
representations. This Agreement can
only be amended by a written agreement signed by you and us. This Agreement shall be interpreted and
enforced under the laws of the province of Ontario, Canada.
BY INSTALLING BajEye, YOU ARE EXPLICITLY AGREEING TO THE
TERMS AND CONDITIONS SET WITHIN.




















